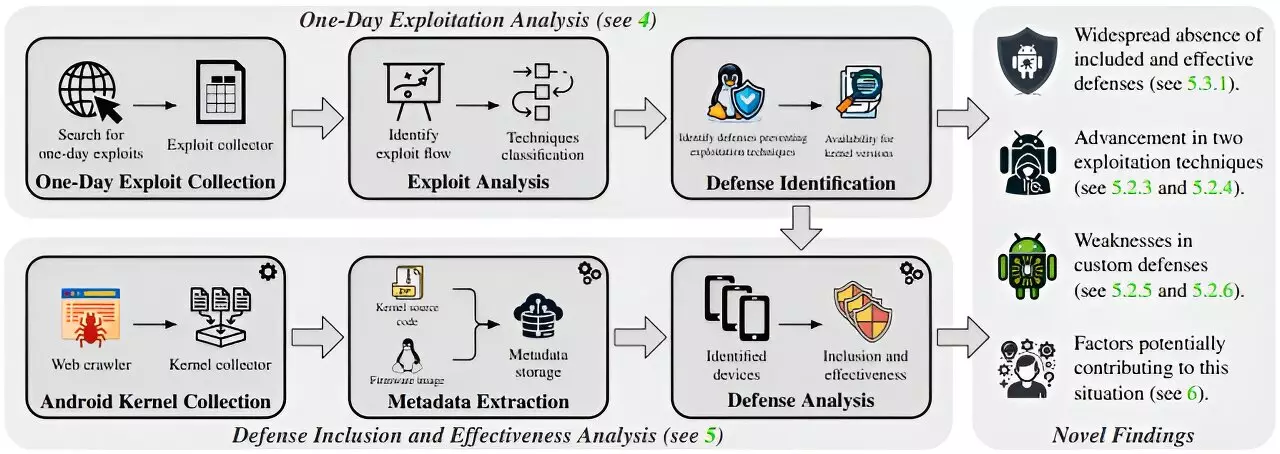
Smartphones have transformed into indispensable tools in our daily lives, functioning not only as communication devices but also as reliable partners in managing personal and professional responsibilities. As they evolve, however, so do the challenges regarding their security. Recent research from the Institute of Applied Information Processing and Communications at Graz University of Technology (TU Graz) highlights a concerning issue: many Android smartphones contain kernel vulnerabilities that can be exploited using established attack strategies, even with existing protective measures in place. The implications of this research prompt a widespread reevaluation of security protocols in the smartphone industry.
The study covers a comprehensive analysis of the Android kernels utilized by ten leading smartphone manufacturers, revealing alarming gaps in security. According to researchers Lukas Maar, Florian Draschbacher, Lukas Lamster, and Stefan Mangard, between 29% and 55% of the tested 994 devices failed to adequately defend against known attacks. The stark contrast between various manufacturers is unsettling; for instance, Google’s Generic Kernel Image (GKI) version 6.1 was shown to block approximately 85% of potential attacks—significantly more than the substantial shortcomings exhibited by the proprietary kernels of manufacturers like Xiaomi, Motorola, and Samsung.
This analysis is crucial for understanding the variance in security levels across different smartphone models, ranging from budget to high-end options. It indicates that many devices released between 2018 and 2023 are still vulnerable, despite the advancing technology that accompanies more recent releases. The kernel versions employed varied significantly, with manufacturers relying on outdated kernels offering vastly diminished safety assurances.
Interestingly, the research indicates that effective countermeasures against many prevalent attack strategies do exist; however, they remain underutilized within the manufacturers’ kernels. Incorrect configurations or a complete lack of activation of these protective features leave smartphones predisposed to vulnerabilities. Alarmingly, even a kernel version as old as 3.1 from 2014—with necessary security measures turned on—outperformed close to 38% of the current kernels in use today. This suggests a disturbing trend: that some manufacturers prioritize cost savings and performance over essential security measures in their devices.
Another notable finding from the TU Graz study is the heightened risk associated with low-end smartphone models. These devices, which often come with reduced processing power and resource constraints, are approximately 24% more susceptible to attacks than their high-end counterparts. This disparity arises partly from manufacturers opting to disable certain security features to boost performance, exposing users to greater peril. Such a decision raises critical questions about the ethics of sacrificing security for efficiency, particularly among consumers who may be unaware of the implications.
In light of these findings, researchers shared their analysis with the manufacturers involved, leading to a range of responses. Notably, companies such as Google, Motorola, Huawei, and Samsung acknowledged the issues and even issued patches to address identified vulnerabilities. This proactive engagement is commendable, but it also underscores a larger problem within the industry: the need for continuous updates and improvements to security measures on all devices, not just those with higher profit margins.
Moreover, researchers have urged Google to revise the Android Compatibility Definition Document (CDD) to elucidate security requirements more clearly. This call for reform illustrates a gap in intentional security practices within Android’s ecosystem and emphasizes the need for ongoing collaboration among manufacturers and developers to ensure user safety.
As smartphones increasingly engage with sensitive tasks such as online banking and official communications, the imperative for robust security measures is paramount. The troubling findings from TU Graz serve as a wake-up call for manufacturers to collaborate and enhance the security posture of their devices. The integration of updated kernel security measures is essential to protect users in a rapidly evolving digital landscape. As technology continues to advance, it must be accompanied by an equally strong commitment to security, ensuring that as smartphones become more powerful, they also become more secure. The call to action is clear: the time for transformative change in smartphone security is now.